12 Aug 2010
I have just released a new version (0.2) of ssltest.pl.
This newest set of changes to the tool still don't include some of the things on my future wishlist, as mentioned in the previous post, but instead came about when I attempted to use the tool from a Windows system and found it didn't work so well.
The changes in version 0.2 were essentially focused on getting the same functionality from the tool when run in Windows, as when run from Linux, as well as fixing some little niggles I found when attempting to use greppable output after running the tool on a list of sites via a for loop.
Some detail on the changes made in version 0.2:
- Windows support, including coloured output using Win32::Console::ANSI.
- Helpful error messages provided for missing perl modules, telling you how to remediate the issue. Not much of an issue on Linux really, as most of the required modules are installed by default, but during the process of adding Windows support I discovered that IO::Socket::SSL, Net::SSLeay and Win32::Console::ANSI are all not installed by default AND not available in the ActiveState perl repositories. The error messages will point you in the right direction to remediate the issue on Windows.
- Some text added to the help message about OpenSSL. While testing the tool on Windows I discovered that the misbehaving SSL appliance that triggered me writing this tool in the first place also did not respond well to particular versions of OpenSSL, in this case because the SSLv3 Hello packet was using a slightly different format. Basically I just wanted to raise awareness here that if the tool isn't working for you on a particular system, you may want to try a different version of OpenSSL.
- The format of the grep-able output has been improved, to include all of the relevant data on each individual line of output, including the compliance status for individual ciphers, hostname and port, protocol (SSLv2, SSLv3, TLSv1), cipher name and cipher description. Essentially this makes the tool easier to use on large numbers of hosts at once - you can test multiple sites from a script, write all the data to one file and then grep the output to find relevant data.
- Some minor cosmetic adjustments.
Here's a screenshot of the tool running on Windows, in all its colourful glory.
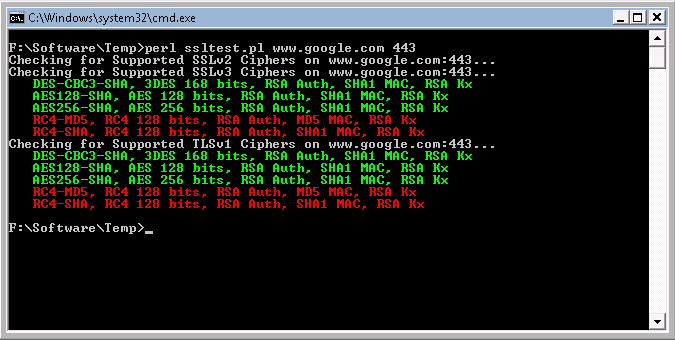
Download it here from Github:
27 Jul 2010
Update: I have just updated this tool to version 0.1.1 to resolve a minor bug (thanks Gitsnik) and a few cosmetic issues.
I have used a number of different tools to check cipher support on SSL Servers, including SSLDigger, sslthing, Cryptonark, Openssl and even a few web based solutions. Each tool has its good and bad points, but recently when trying to confirm that a particular badly behaved reverse proxy was compliant with DSD ISM crypto standards I ran into some problems. The reverse proxy I was attempting to test was not correctly responding to or closing SSLv2 and TLSv1 sessions, causing a number of the tools that I commonly use to freeze up.
Cryptonark was able to run against the proxy without freezing up, due to its ability to timeout sessions, but it still wasn't providing the right results due to the fact that it only tests SSLv2 and TLSv1, but not SSLv3 - the only protocol that happened to work on this particular system. The tool is written in Perl however, so I consequently decided to quickly modify it to test SSLv3 as well.
But what started off as a quick modification, soon turned into a complete rewrite, as I rapidly came up with a list of additional features I wanted in addition to the SSLv3 support - optional verbose output (such as listing unsupported ciphers, plus connection attempts), colour highlighting for DSD ISM compliance as well as PCI-DSS, control over timeout settings, the ability to individually test protocols, more detail in the explanatory text for each cipher, greppable compliance status for each cipher, etc. I have essentially reused the essential design concepts of the Cryptonark tool (including colour coding output, use of IO::Socket::SSL to make SSL connections, documenting supported ciphers within the tool, checking supported ciphers against a compliance standard), but have completely rewritten the code from scratch to clean it up, reduce repetition and dependence on additional perl modules, and ease implementation of the new features.
So now the tool is complete, it includes all those additional features I wanted, and it works very nicely against that badly behaving reverse proxy that started this whole thing.
I have decided to make the tool available here, first of all so I can easily get to a copy when needed, and also just in case anyone else finds it useful. Until I can think of something better, I'm releasing this under the imaginative name of ssltest.pl - so called because the tool is used to test ssl.
Here is a listing of the help:
lupin@lion:~$ ssltest.pl
ssltest 0.1.1
grey-corner.blogspot.com
Tests the provided SSL host to determine supported SSL protocols and ciphers.
Originally based on Cryptonark by Chris Mahns.
USAGE:
/home/lupin/bin/ssltest.pl [options] host port
/home/lupin/bin/ssltest.pl [--pci|--ssl2|--ssl3|--tls1] --list
OPTIONS:
-v|--verbose Verbosity level. Use once to also list tested
ciphers that are not enabled on the target host.
Use twice to also show when host connection
attempts are made.
-r|--ssl2 Performs cipher tests for the sslv2 protocol.
Default is all protocols (ssl2, ssl3, tls1).
-s|--ssl3 Performs cipher tests for the sslv3 protocol.
Default is all protocols (ssl2, ssl3, tls1).
-t|--tls1 Performs cipher tests for the tlsv1 protocol.
Default is all protocols (ssl2, ssl3, tls1).
-x|--timeout Sets timeout value in seconds for connections.
Default 4. Lower value for hosts that may not
properly close connections when an unsupported
protocol request is attempted. Raise value for
slow links/hosts.
-i|--ism Marks enabled ciphers that are compliant with the
DSD ISMs standards for in-transit protection of
IN-CONFIDENCE information (ISM Sep 2009). Default
compliance standard used (as opposed to PCI).
-p|--pci Marks enabled ciphers that are compliant with
PCI-DSS standards. Provided as an alternate
compliance standard to the DSD ISM.
-g|--grep Outputs in a semicolon ";" separated greppable
format, adds text for compliance status. Use
when you need to write output to a text file and
you want compliance status to be included in
text format instead of just being repressnted by
terminal colour.
-l|--list Lists ciphers checked by this tool and exits,
with output colour coded to indicate compliance
status with the selected standard (pci or ism).
Host and port values do not need to be provided
when using this option, as no host connection is
made. Purely informational, so you can see what
ciphers are tested for, and which are deemed to be
compliant with the various standards.
If one or more protocol/s (SSLV2, SSLV3, TLSV1) are not specifically enabled,
tests for all protocols will be performed. If you know that a host does not
support certain protocols (or does not properly close connection attempts made
using particular protocols) you can only include tests for the protocols you
are interested in to speed up the test. If no compliance standard is
specifically enabled, or if more than one standard is enabled, the default
is to use the DSD ISM.
EXAMPLES:
/home/lupin/bin/ssltest.pl -vvrsi test.example.com 443
Performs testing on host test.example.com port 443, using the sslv3 protocol
(-s), and sslv2 protocol (-r), matches responses against the cipher
requirements in the ISM (-i) and provides double verbose output (-vv) where
ciphers unsupported by the destination host and connection attempts are printed
to screen.
/home/lupin/bin/ssltest.pl --list
Provides a list of all ciphers supported by the tool, colour coded to indicate
which ones are considered to be compliant with the ISM. Add the --pci switch
to colour code listed ciphers for PCI compliance instead, or supply the --ssl2,
--ssl3 or --tls1 switches to only list ciphers appropriate to those protocols.
Here is the tool in action, performing a test of the SSL ciphers supported by www.google.com
lupin@lion:~$ ssltest.pl www.google.com 443
Checking for Supported SSLv2 Ciphers on www.google.com:443...
Checking for Supported SSLv3 Ciphers on www.google.com:443...
DES-CBC3-SHA, 3DES 168 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
AES128-SHA, AES 128 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
AES256-SHA, AES 256 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
RC4-MD5, RC4 128 bits, RSA Authentication, MD5 MAC, RSA Key Exchange
RC4-SHA, RC4 128 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
Checking for Supported TLSv1 Ciphers on www.google.com:443...
DES-CBC3-SHA, 3DES 168 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
AES128-SHA, AES 128 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
AES256-SHA, AES 256 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
RC4-MD5, RC4 128 bits, RSA Authentication, MD5 MAC, RSA Key Exchange
RC4-SHA, RC4 128 bits, RSA Authentication, SHA1 MAC, RSA Key Exchange
I have reproduced above the colour coding the tool uses, a really helpful feature "borrowed" from Cryptonark, showing which ciphers are considered to be supported under the DSD ISM. You can see from the above output that no SSlv2 ciphers are supported, and that some ciphers are coloured green, indicating that they are compliant with the selected standard of the ISM, and others are coloured red, indicating they are not.
Some ideas I have for the next revision of this tool are to have it verify that the hostname matches the common name on the certificate, to confirm the certificate has not expired, and possibly also to verify that the certificate is signed by a trusted certificate authority and has not been revoked.
You can download version the tool from Github:
Let me know if you try this tool out and find it useful.

